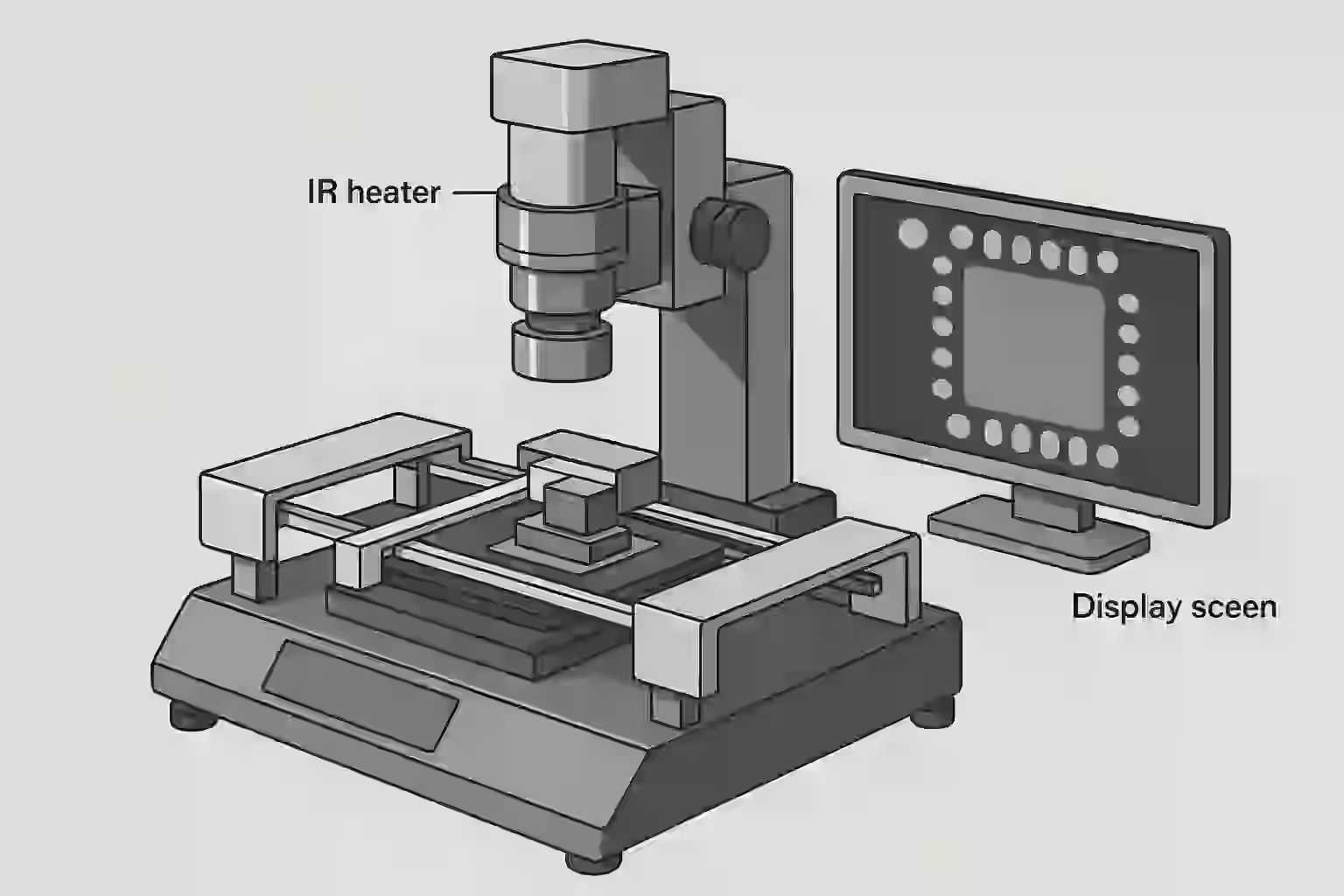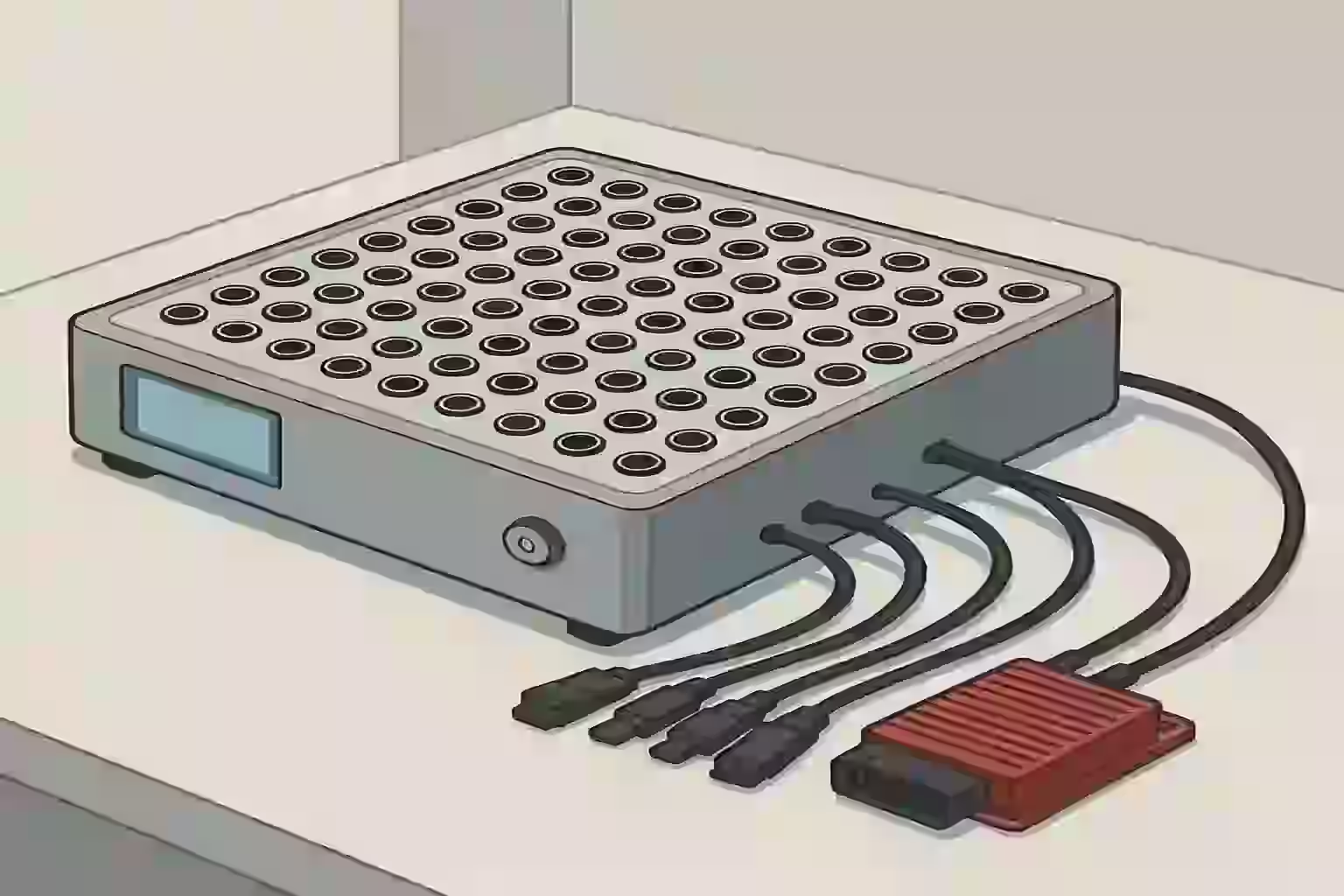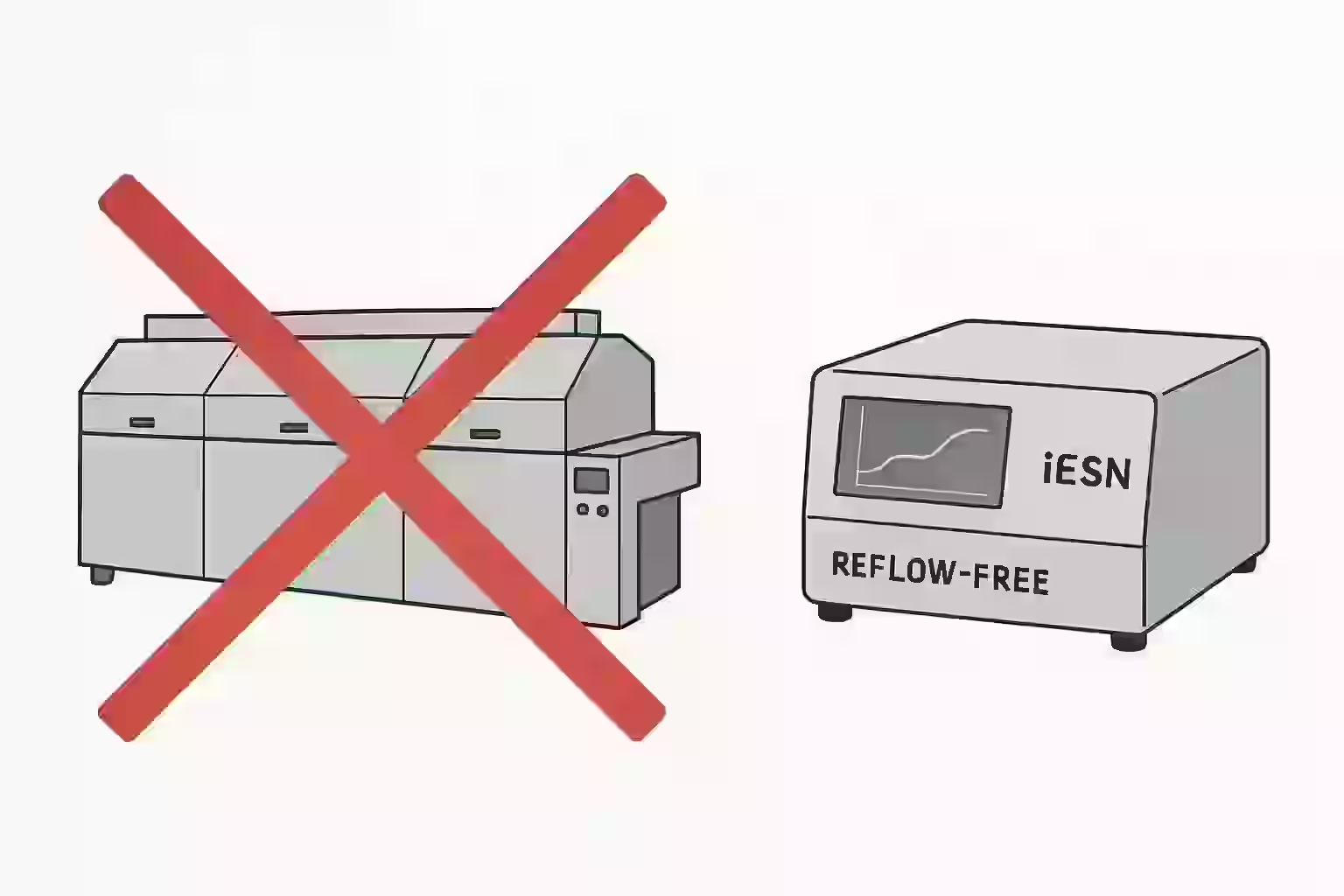
The Concepts - Where It All Began
Every tool, standard, and product we build starts here — with a raw, unresolved idea grounded in reality. It starts with a dream — the kind of dream that once changed the world. These aren’t theories. They’re professional frustrations transformed into structured, scalable concepts.
Real concepts, built on real needs. The starting point of a future product.
See our dreams
The Projects - Real Life of Dreams
This is where ideas leave the notebook and face the real world — tested not in theory, but in practice. Every project is a testbed — a living experiment that transforms ambition into reality. It’s the place where frustration meets refinement, where all the back and forth ends — and perfection is born.
Because a dream means nothing until it lives. Proves that science became practical.
See Our Projects

The Products - All Comes Together
Products are the result of everything that came before: ideas, concepts, testing, failures, and breakthroughs. Built for professionals, not mass markets — grounded in science, shaped by frustration, and refined through use. It was a long way. The place where the innocent idea becomes the real game changer.
Where real tools replace promises — with science, and nothing else.
Browse Products
Collaborate - Minds Connect
Collaboration is more than teamwork. It's shared frustration turned into shared progress. At iESN, professionals don’t compete — they contribute. Every idea, every insight, every mistake shared strengthens the whole. Because in our field, true advancement doesn’t happen alone. It must be connected
One problem. One solution. Many minds. One of the many secrets behind iESN
Join the Collaboration

Sustainability - iESN meets Earth
Sustainability at iESN isn’t marketing — it’s our design principle. We rethink how electronics are made, used, and repaired so that they serve longer, waste less, and stay out of landfills. Because a smarter system must also be a lighter one — on the planet, and on the future. Glad te meet you Earth!
The future must be repairable - or it won’t exist. No more intellectual promiscuity.
Our Commitment

Financial — Fueling What Matters
At iESN, financial strategy isn’t just spreadsheets — it’s how we decide what deserves to exist. We fund precision, not popularity. We invest in ideas that fix real problems, not those that fit trends. Because innovation dies when money ignores the mission. Financing the real values!
Not market-driven — mission-funded. From dream to product, that’s what matters.
Visit the Help Center

Help Center - Map to Everything
The Help Center isn’t just support — it’s orientation. It connects every part of iESN: from concepts to ecosystem, from philosophy to product, from menu to footer. It explains what you see and what you don’t - the structure behind the site, the logic behind the tools, and the ideas behind the words.
Because real help explains — not just answers.
Visit the Help Center
About Us — (It Can Be About You)
p>iESN isn’t just a project. It’s a call to those who believe electronics should be better — clearer, more repairable, more professional. We’re not here to impress. We’re here to improve. And if that resonates with you — maybe this isn’t just about us. It’s about 35+ years of real, complex electronics.
Clarity, purpose, and the courage to do it differently. Be part of the Revolution
Meet iESN (Meet You)
Ecosystem - Everything Connects
The iESN Ecosystem is more than a collection of tools — it’s a living structure where standards, software, hardware, people, and data work together. Each part reinforces the others. Each node shares what it knows. It’s how concepts become standards, projects become products. It is the root.
Not just a system, not just another website — a structure for progress.
Enter the Ecosystem